Identity 101
I figured no better first post on this new experimental blog than my take on an IAM 101 primer. But, first a little dialogue:
Random Person: So, what do you do for a living?
Me: I’m an identity and access management professional.
Random Person: Oh. What is that? Is it like identity theft stuff?
Me: Maybe. Sort of. Actually not really.
Random Person: Um, ok.
Me: Think about it like this, you sign-in to your bank using a username and password, right?
Random Person: Yeah.
Me: Well, I design similar systems that allow you to securely sign-in to your bank account as an example. And in doing so, the bank can obtain an acceptable level of assurance that you are actually are who you claim to be. This would be the “identity” aspect of things. And once you’re signed-in (authenticated), you and only you, can see your balances, pay bills, transfer funds, etc from you account. This would be the “access” aspect, essentially what you’re authorized to do.
Random Person: Ahhh! Sounds cool… **slightly confused look**
I’m fairly certain a similar conversation happened when I met my wife for the very first time. Otherwise, this is a framework of a common conversation I’ve had several times over the past 16 years or so. I’m certain any identity professional could share similar experiences. However, more recently, these types of conversations seem to be getting easier- almost like the average everyday person is starting to better understand the basic concepts around digital identity. Especially as the world around us is experiencing an exponential growth of digital experiences requiring some form of proper authentication and authorization.
I recently went to Claude and asked: Can you provide me an easy to understand definition of “Identity and Access Management?” I was quite satisfied with the response:
Identity and Access Management (IAM) is a security pillar that deals with controlling and managing who has access to what resources within an organization or system. It involves three main components: identification, authentication, and authorization.
The primary goal of IAM is to ensure that only authorized individuals or systems can access sensitive data, applications, and other resources within an organization, while preventing unauthorized access. It helps maintain data confidentiality, integrity, and availability, which are crucial aspects of information security.
I personally, like to define Identity and Access Management as the set of people, processes, and technologies that enable accurate identification of users through strong authentication methods, while ensuring they can access only the resources they are authorized to. What encompasses these processes and technologies is where it can get fun and complicated at the same time. One thing I love most about IAM is it’s ability to not only be a set of security controls to protect any enterprise, but it can be critical business enabler for any organization as well.
I started my career in the financial services industry and it’s here where I made a transition from a software engineering team to the wonderful world of identity. I think because of this, my initial perspective of identity was 100% about security controls and introducing as much friction as humanly possible. These were also the days that perimeter security was everything! I could remember getting denied to purchase additional Quest Change Auditor license, meanwhile the firewall and VPN teams were spending millions hand over fist. The good ol’ days… Anyway identity focused standards and policies drove what “will” happen versus what “could” or “should” happen. It wasn’t until several years later, in a completely different industry, that business enablement was actually more important than introducing such high levels of friction, from an identity stance. All of a sudden I had to fully grasp the underlying business aspects of things to really be successful in building an identity program. Need several millions dollars to go modernize something? You better make sure you fully understand how this will enhance the user experience and ultimately drive positive business outcomes. Otherwise, try again.
But, back to identity, there’s two fundamental core aspects to IAM that are paramount to understand and that’s authentication (aka authN) and authorization (aka authZ). In it’s simplest forms:
-
Authentication: verifies who the user is claiming to be. As in, who are you?
-
Authorization: determines what resources and data a user can access. As in, what can you do?
Now let’s dive much deeper into all aspects of Identity and Access Management. I like to break down IAM into 8 components and several functions within these components.
- Identity Management: involves the processes and technologies used to recognize, authenticate, and authorize individuals to access systems and data within an organization
- Authentication: verifies a user’s identity through credentials like passwords, biometrics, or tokens before granting access to systems and services.
- Authorization: determines what resources or actions a verified user is allowed to access or perform within a system.
- User Store (Directory Service): a centralized database that stores and manages information about users, groups, and devices within an organization’s network.
- Identity Federation: allows different organizations to share identity information, enabling users to access multiple systems and services with a single set of credentials.
- Identity Governance & Administration (IGA): involves the policies, processes, and technologies used to manage user identities and control access to resources in compliance with security and regulatory requirements.
- Privileged Access Management (PAM): secures, controls, and monitors access to an organization’s critical resources and systems by privileged users or accounts.
- Audit and Compliance: involves reviewing and ensuring that an organization’s processes and transactions meet established standards and regulatory requirements.
To help visualize and break this down even further into the functional aspects of the 8 pillars, here’s a mind map:
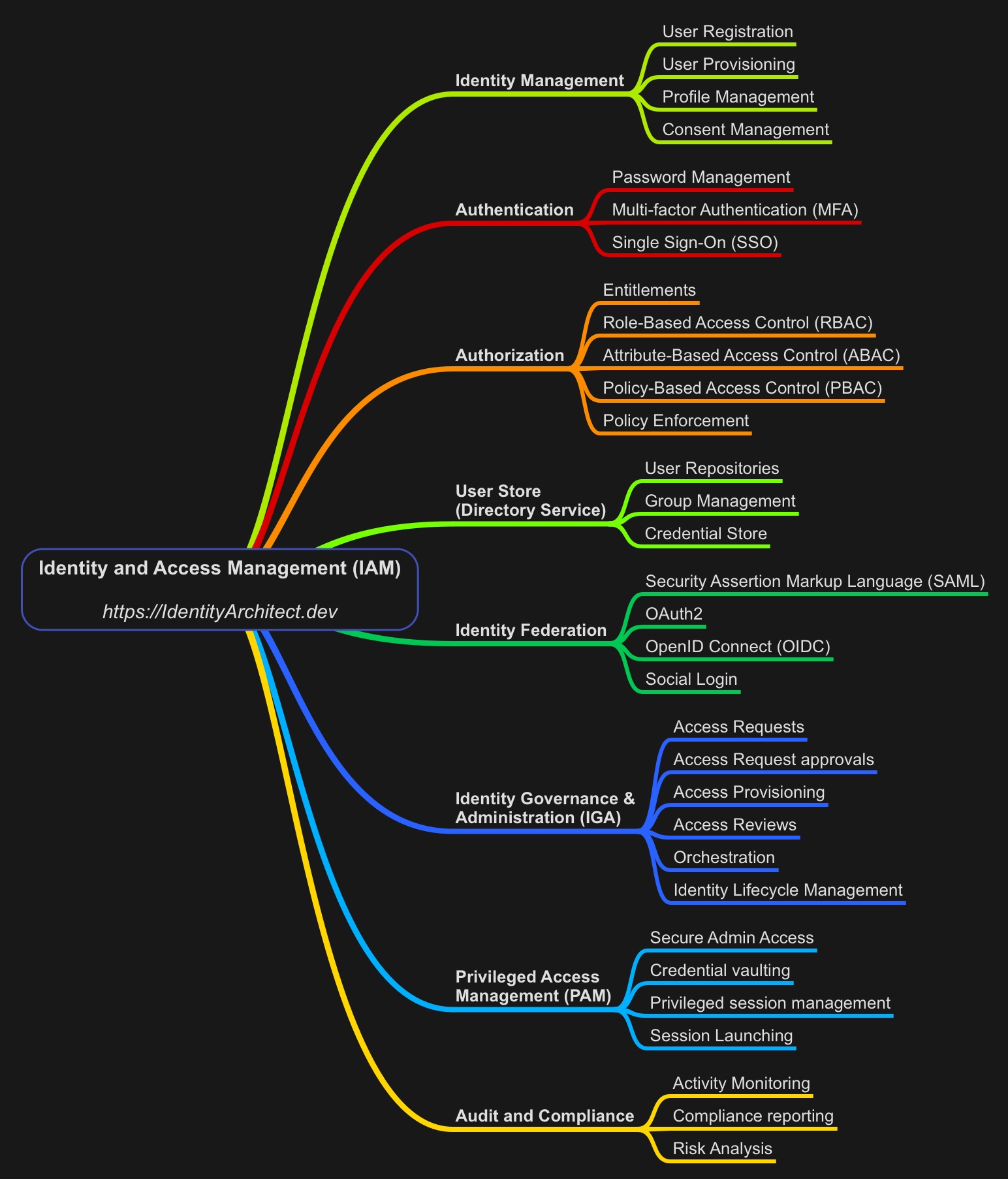
For this post, I won’t go into further detail of the individual functions and the role they play, but I did create a much larger mind map that provides a high level description of the mentioned functions. You can download a PDF version here.
In summary, username and password is just the tip of the iceberg when is comes to Identity and Access Management. There’s a lot of moving pieces and it can get complicated pretty fast. One of many things I love about the identity space, is no matter if you’re new to this or a 20 year veteran, there’s always more to learn!
If you’re looking to find out even more about the identity space, I highly recommend looking into joining IDPro and follow the Identity Jedi Newsletter.